Foreign followers
5000
GLOBAL CRITICAL INFRASTRUCTURE
The assets, systems, networks, facilities and other elements the world relies upon, whether physical or cyber, that are so vital that their incapacity or destruction would have a debilitating impact to global security, economies, and public health and safety.
MOVING FROM A 'REACTIVE' TO A 'PROACTIVE' SECURITY STRATEGY
Requires Informed Defenders to Enable and Sustain Security Resilience
IDENTIFY - DETECT - PROTECT - RESPOND - RECOVER
The best "PROACTIVE DEFENSE' is the collective public- and private-sector identification, analysis and information sharing of
globally trusted all-hazards "ACTIONABLE" intelligence, defense measures supported by coordinated response.

Commercial Design


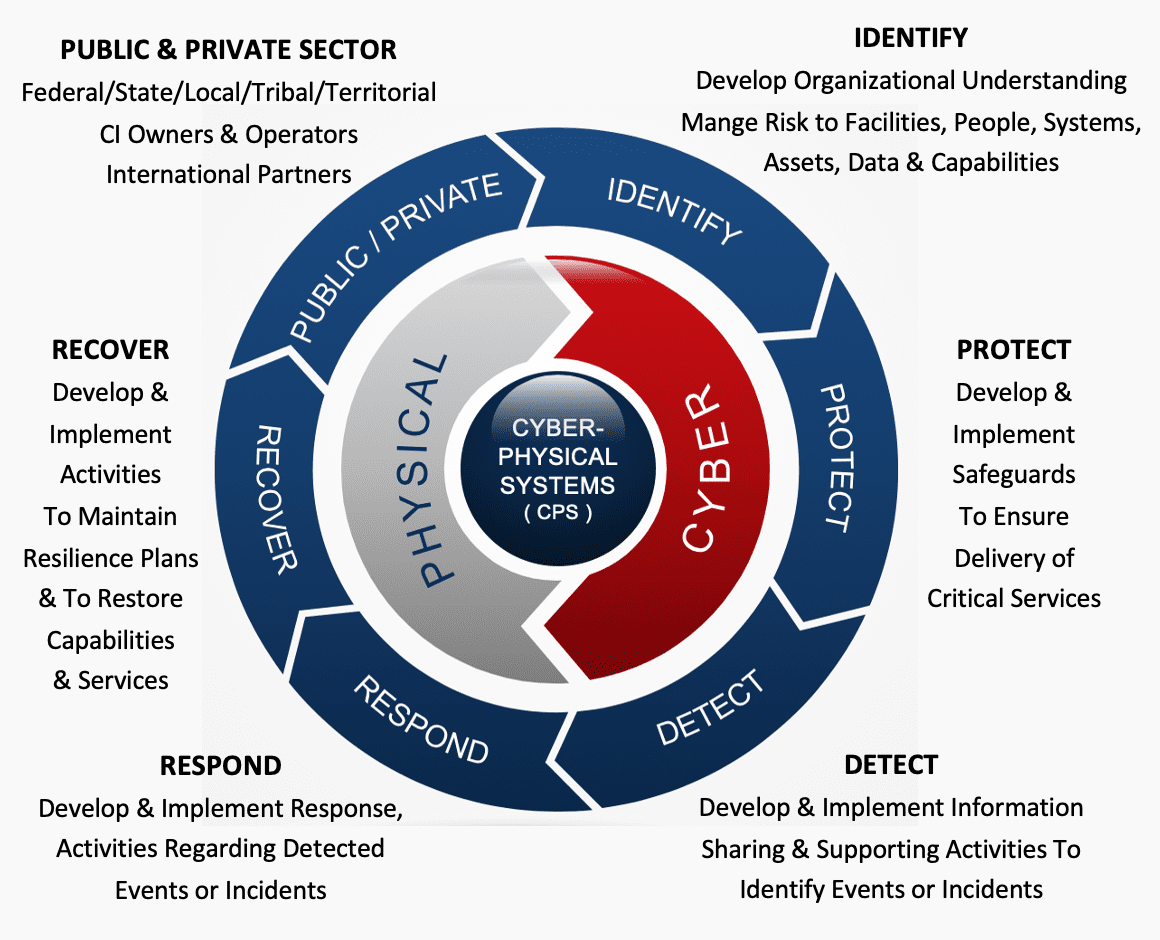 | SECURITY CONVERGENCE ALIGNMENT - PHYSICAL, CYBER, CYBER-PHYSICAL SECURITY Mitigating Risk by Identifying, Protecting, Detecting, Responding & Recovering from Changing Conditions or Adverse Events PHYSICAL SECURITY Protection of People, Property and Physical Assets from Actions or Events That Could Cause Damage or Loss CYBER SECURITY Prevention of Damage to Unauthorized Use or Exploitation of, and If-Needed, the Restoration of Electronic Information & Communication Systems and the Information They Contain to Strengthen Confidentiality, Integrity and Availability CYBER-PHYSICAL SYSTEMS (CPS) SECURITY Protecting Smart Systems That Include Engineering Interacting Networks of Digital, Analog, Physical and Human Components |

PHYSICAL SECURITY - The protection of people, property and physical assets from actions and events that could cause damage or loss.Physical threats include any event such as pandemics, violent civil unrest, climate change, natural disasters, hurricanes, tornadoes, floods, volcanoes, earthquakes, criminal acts, terrorism, and weapons of mass destruction.PHYSICAL SECURITY RESILIENCE - An organization's ability to prevent, to the greatest degree possible, the loss of, theft, or damage to assets (people, information, equipment, facilities, activities and operations) from threats and vulnerabilities.
Maintaining a strong physical security resilience posture requires continual situational awareness and evaluation of existing, new and changing risks -
Asset Management - Identification, and assessment to an asset's nature and value and the degree of impact if damaged or lostThreat Management - Identification of threats that are indications, circumstances or events with the potential to cause loss of, or damage to an asset or capability, and perceived imminence of environment, physical or criminal aggressionVulnerability Management - Identification of weaknesses, characteristics or circumstances that if left unchanged, may result in being impacted by a natural event or exploited by an adversary that may result in the degradation, loss of life, or damage to mission-essential resourcesRisk Management - Once assets, threats and vulnerabilities are identified, conducting a risks analysis to determine the impact of an unwanted event and the likelihood that it will happen.Countermeasure Management - Based upon calculated risks, countermeasures and security measures are defined to be employed to protect assets

CYBERSECURITY - Encompasses the technologies, activities, processes, abilities, capabilities, resources and state whereby information, communications, and cyber-physical systems are protected against damage, unauthorized use, modification or exploitation.
An Attack . . . is an Attack . . . is an Attack - Threatening All Critical Infrastructure Sectors, Communities and Government - Cyber attacks may initially occur or originate in one sector, but can quickly cascade impacting other sectors.. While cyber defenders are focused on specific sectors, adversaries are focusing attacks on IP ranges and vulnerabilities 99% of the time. A cyber attack on any sector must include monitoring and analyzing threat impacts across all sectors to identify attacks that will (eventually) be made against others.
IACI Global Common Operational Picture (COP) - IACI's all-hazards global monitoring and reporting encompasses all critical infrastructure sectors, government, law enforcement and other communities.
CYBERSECURITY RESILIENCE - An organization's ability to continuously deliver critical services services, operations and outcomes despite the occurrence of incidents
or events via:
- Asset Management - Identification, documentation and management of critical assets during their lifecycle ensuring sustained critical services
- Control Management - identification, analysis and management of controls enabling critical services operations
- Configuration & Change Management - Processes to ensure the assets integrity, using change control and change control audits
- Threat & Vulnerability Management - Identification, detection, analysis, reduction and deterrence to ensure critical services integrity and availability
- Incident Response Management - Response, resiliency and recovery policies, processes and activities to identify and analyze events, detect incidents, and determine activation of response protocols.
- Service Continuity Management - Enduring the continuity of essential operations of services and associated assets if a disruption occurs
- Risk Management - Strategy, policy, standards and Identification, analysis and mitigation of risks to critical assets that could adversely affect service operation and delivery
- Situational Awareness - Encompassing access to global public- and private-sector discovery and analysis of timely and actionable threat and defensive measures intelligence from trusted sources related to immediate operatioal and service stability, reliability and security
- External Dependencies Management - Processes to manage the appropriate level of controls to ensure sustainment and protection of services and assets dependent on the actions of external entities
- Best Practice Adoption, Training & Awareness- Development of skills and promoting awareness for people with roles that support critical services and operations

SMART SYSTEMS - INTERACTING PHYSICAL & CYBER COMPONENTS
These highly interconnected and integrated systems and services provide new functionalities
to improve quality of life and enable technological advances.
CPS SECURITY - The ability to ensure CPS capabilities are not compromised by
malicious agents, and that the information used, processed, stored and transferred
has its integrity preserved and is kept confidential where needed, and that CPS
architecture is resilient to interoperability, scalability, and changing situations.
CYBER-PHYSICAL SYSTEMS & CONNECTED SERVICES (INTERNET-OF-THINGS)
- Buildings Commercial/Institutional (Office, Education, Retail, Hospitality, Healthcare, Airports, Stadiums, Government); Industrial (Process, Clean Room, Campus); Devices ( HVAC, Transport, Fire & Safety, Lighting, Security, Access, etc.)
- Consumer & Home Infrastructure Infrastructure (Wiring, Network Access, Energy Management); Awareness & Safety (Security/Alerts, Fire Safety, Environmental Safety, Safety for People with Disabilities, the Elderly, Children, Power Protection); Convenience & Entertainment(HVAC, Climate, Lighting, Appliance, Entertainment); Devices (Digital Cameras, Power Systems, MID, eReaders, Desktop Computers, Appliances, Meters, Lights, TVs, Audio, Games, Consoles, Lighting, Alerts
- Energy Supply/Demand (Power Generators, Transportation & Distribution, Low Voltage, Power Quality, Energy Management), Alternative (Solar, Wind, Co-Generation, Electrochemical); Oil Gas (Rigs, Derricks, Well Heads, Pumps, Pipelines); Devices (Turbines, Windmills, UPS, Batteries, Generators, Meters, Drills, Fuel Cells, etc.)
- Healthcare & Life Sciences Care (Hospital, ER, Mobile POC, Clinics, Labs, Doctors Offices); In Vivo/Home (Implants, Home Monitoring Systems); Research (Drug, Discovery, Diagnostics, Labs); Devices (Medical Devices, MRI, PDAs, Implants, Surgical Equipment, Pumps, Monitors, Telemedicine, etc.)
- Industrial Resource Automation (Mining, Irrigation, Agricultural, Woodland); Fluid/Processors (Petrochemical, Hydro Carbon, Food/Beverage); Converting/Discrete (Metals, Paper, Rubber/Plastic, Metalworking, Electronics, Assembly/Test); Distribution (Pipelines, Material Handling, Conveyance); Devices (Pumps, Valves, Vats, Conveyors, Pipelines, Motors, Drives, Converting, Fabrication, Assembly/Packaging, Vessels/Tanks, etc.
- IT & Communication Networks Public (Services, E-Commerce, Data Centers, Mobile Carriers, Fixed Carriers, ISPs); Enterprise (IT/Data Center, Office, Private Networks); Devices (Servers, Storage, PCs, Routers, Switches, PBXs, etc.
- Retail Specialty (Fuel Stations, Gaming, Bowling, Cinemas, Nightclubs/Dancing, Sports, Concerts, Special Events); Hospitality (Hotels, Resorts, Theme Parks, Restaurants, Bars, Cafes, Clubs); Stores (Supermarkets, Shopping Centers, Single Site, Distribution Centers); Devices (POS Terminals, Tags, Cash Registers, Vending Machines, Signs, etc.)
- Security Public Safety Surveillance (Radar/Satellite, Environmental, Military Security, Unmanned Systems, Fixed); Equipment (Weapons, Vehicles, Ships, Aircraft, Gear); Tracking (Human, Animal, Postal, Food, Health, Packaging, Baggage); Public Infrastructure (Water Treatment, Building, Environmental, Generators, Environ, Surveillance); Emergency Services (Equipment & Personnel, Police, Fire, First Responders, Regulatory); Devices (Tanks, Fighter Jets, Battlefield COMS Jeeps, Cars, Ambulances, Breakdown/Lane Worker, Homeland Security, Fire, Environmental, Monitoring, etc.
- Transportation Non-Vehicular (Air, Rail, Maritime); Vehicles (Consumer, Commercial, Construction, Off-Highway); Transportation Systems (Tools, Traffic Management, Navigation, Public Transportation); Devices (Vehicles, Lights, Ships, Planes, Signage, Tolls, etc.)